Docker For Mac Disable Fsync
Welcome to Docker Desktop!
The Docker Desktop for Mac section contains information about the Docker Desktop Community Stable release. For information about features available in Edge releases, see the Edge release notes. For information about Docker Desktop Enterprise (DDE) releases, see Docker Desktop Enterprise.
Here is what worked for me to get rid of the red notification ballon and still have access to System Preferences from the dock. Replace the Systems Preferences icon on the dock with its Alias: Remove System Preferences icon from dock (either drag icon off dock or right-click on it and choose 'Options' and then 'Remove from Dock').
Docker is a full development platform to build, run, and share containerized applications. Docker Desktop is the best way to get started with Docker on Mac.
See Install Docker Desktop for download information, system requirements, and installation instructions.
Check versions
Ensure your versions of docker and docker-compose areup-to-date and compatible with Docker.app. Your output may differ if you arerunning different versions.
Explore the application
Open a command-line terminal and test that your installation works byrunning the simple Docker image,hello-world:
Start a Dockerized web server. Like the
hello-worldimage above, if theimage is not found locally, Docker pulls it from Docker Hub.In a web browser, go to
http://localhost/to view the nginx homepage.Because we specified the default HTTP port, it isn’t necessary to append:80at the end of the URL.Early beta releases used
dockeras the hostname to build the URL. Now,ports are exposed on the private IP addresses of the VM and forwarded tolocalhostwith no other host name set.View the details on the container while your web server is running (with
docker container lsordocker ps):Stop and remove containers and images with the following commands. Use the“all” flag (
--allor-a) to view stopped containers.
Preferences
Choose the Docker menu > Preferences from themenu bar and configure the runtime options described below.
General
On the General tab, you can configure when to start and update Docker:
Start Docker Desktop when you log in: Automatically starts Docker Desktop when you open your session.
Automatically check for updates: By default, Docker Desktop automatically checks for updates and notifies you when an update is available. You can manually check for updates anytime by choosing Check for Updates from the main Docker menu.
Include VM in Time Machine backups: Select this option to back up the Docker Desktop virtual machine. This option is disabled by default.
Securely store Docker logins in macOS keychain: Docker Desktop stores your Docker login credentials in macOS keychain by default.
Send usage statistics: Docker Desktop sends diagnostics, crash reports, and usage data. This information helps Docker improve and troubleshoot the application. Clear the check box to opt out.
Click Switch to the Edge version to learn more about Docker Desktop Edge releases.
Resources
The Resources tab allows you to configure CPU, memory, disk, proxies, network, and other resources.
Advanced
On the Advanced tab, you can limit resources available to Docker.
Advanced settings are:
CPUs: By default, Docker Desktop is set to use half the number of processorsavailable on the host machine. To increase processing power, set this to ahigher number; to decrease, lower the number.
Memory: By default, Docker Desktop is set to use 2 GB runtime memory,allocated from the total available memory on your Mac. To increase the RAM, set this to a higher number. To decrease it, lower the number.
Swap: Configure swap file size as needed. The default is 1 GB.
Disk image size: Specify the size of the disk image.
Disk image location: Specify the location of the Linux volume where containers and images are stored.
You can also move the disk image to a different location. If you attempt to move a disk image to a location that already has one, you get a prompt asking if you want to use the existing image or replace it.
File sharing
Use File sharing to allow local directories on the Mac to be shared with Linux containers.This is especially useful forediting source code in an IDE on the host while running and testing the code in a container.By default the /Users, /Volume, /private, /tmp and /var/folders directory are shared. If your project is outside this directory then it must be addedto the list. Otherwise you may get Mounts denied or cannot start service errors at runtime.
File share settings are:
Add a Directory: Click
+and navigate to the directory you want to add.Apply & Restart makes the directory available to containers using Docker’sbind mount (
-v) feature.There are some limitations on the directories that can be shared:
- The directory must not exist inside of Docker.
For more information, see:
- Namespaces in the topic onosxfs file system sharing.
- Volume mounting requires file sharing for any project directories outside of
/Users.)
Proxies
Docker Desktop detects HTTP/HTTPS Proxy Settings from macOS and automaticallypropagates these to Docker and to your containers. For example, if you set yourproxy settings to http://proxy.example.com, Docker uses this proxy whenpulling containers.
When you start a container, your proxy settings propagate into the containers.For example:
You can see from the above output that the HTTP_PROXY, http_proxy, andno_proxy environment variables are set. When your proxy configuration changes,Docker restarts automatically to pick up the new settings. If you have anycontainers that you would like to keep running across restarts, you should consider using restart policies.
Network
You can configure Docker Desktop networking to work on a virtual private network (VPN). Specify a network address translation (NAT) prefix and subnet mask to enable Internet connectivity.
Docker Engine
The Docker Engine page allows you to configure the Docker daemon to determine how your containers run.
Type a JSON configuration file in the box to configure the daemon settings. For a full list of options, see the Docker Enginedockerd commandline reference.
Click Apply & Restart to save your settings and restart Docker Desktop.
Command Line
On the Command Line page, you can specify whether or not to enable experimental features.
Experimental features provide early access to future product functionality.These features are intended for testing and feedback only as they may changebetween releases without warning or can be removed entirely from a futurerelease. Experimental features must not be used in production environments.Docker does not offer support for experimental features.
To enable experimental features in the Docker CLI, edit the config.jsonfile and set experimental to enabled.
To enable experimental features from the Docker Desktop menu, clickSettings (Preferences on macOS) > Command Line and then turn onthe Enable experimental features toggle. Click Apply & Restart.
For a list of current experimental features in the Docker CLI, see Docker CLI Experimental features.
On both Docker Desktop Edge and Stable releases, you can toggle the experimental features on and off. If you toggle the experimental features off, Docker Desktop uses the current generally available release of Docker Engine.
You can see whether you are running experimental mode at the command line. IfExperimental is true, then Docker is running in experimental mode, as shownhere. (If false, Experimental mode is off.)
Kubernetes
Docker Desktop includes a standalone Kubernetes server that runs on your Mac, sothat you can test deploying your Docker workloads on Kubernetes.
The Kubernetes client command, kubectl, is included and configured to connectto the local Kubernetes server. If you have kubectl already installed andpointing to some other environment, such as minikube or a GKE cluster, be sureto change context so that kubectl is pointing to docker-desktop:
If you installed kubectl with Homebrew, or by some other method, andexperience conflicts, remove /usr/local/bin/kubectl.
To enable Kubernetes support and install a standalone instance of Kubernetesrunning as a Docker container, select Enable Kubernetes. To set Kubernetes as thedefault orchestrator, select Deploy Docker Stacks to Kubernetes by default.
Click Apply & Restart to save the settings. This instantiates images required to run the Kubernetes server as containers, and installs the
/usr/local/bin/kubectlcommand on your Mac.When Kubernetes is enabled and running, an additional status bar item displaysat the bottom right of the Docker Desktop Settings dialog.
The status of Kubernetes shows in the Docker menu and the context points to
docker-desktop.By default, Kubernetes containers are hidden from commands like
dockerservice ls, because managing them manually is not supported. To make themvisible, select Show system containers (advanced) and click Apply andRestart. Most users do not need this option.To disable Kubernetes support at any time, clear the Enable Kubernetes check box. TheKubernetes containers are stopped and removed, and the
/usr/local/bin/kubectlcommand is removed.For more about using the Kubernetes integration with Docker Desktop, seeDeploy on Kubernetes.
Reset
Reset and Restart options
On Docker Desktop Mac, the Restart Docker Desktop, Reset to factory defaults, and other reset options are available from the Troubleshoot menu.
For information about the reset options, see Logs and Troubleshooting.
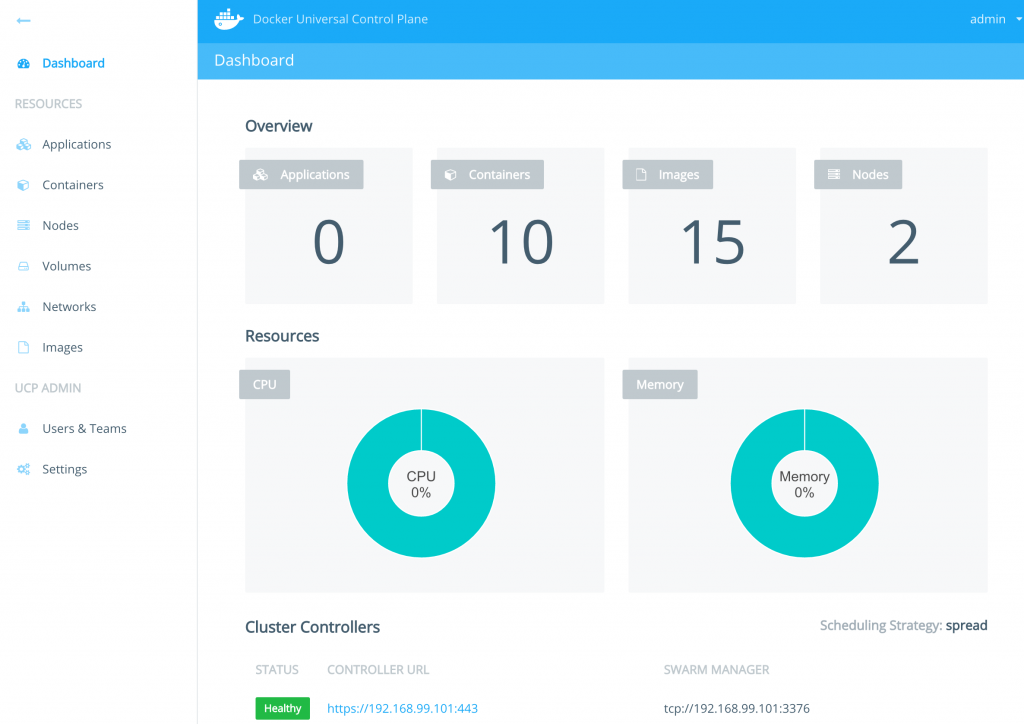
Dashboard
The Docker Desktop Dashboard enables you to interact with containers and applications and manage the lifecycle of your applications directly from your machine. The Dashboard UI shows all running, stopped, and started containers with their state. It provides an intuitive interface to perform common actions to inspect and manage containers and existing Docker Compose applications. For more information, see Docker Desktop Dashboard.
Add TLS certificates
You can add trusted Certificate Authorities (CAs) (used to verify registryserver certificates) and client certificates (used to authenticate toregistries) to your Docker daemon.
Add custom CA certificates (server side)
All trusted CAs (root or intermediate) are supported. Docker Desktop creates acertificate bundle of all user-trusted CAs based on the Mac Keychain, andappends it to Moby trusted certificates. So if an enterprise SSL certificate istrusted by the user on the host, it is trusted by Docker Desktop.
To manually add a custom, self-signed certificate, start by adding thecertificate to the macOS keychain, which is picked up by Docker Desktop. Here isan example:
Or, if you prefer to add the certificate to your own local keychain only (ratherthan for all users), run this command instead:
See also, Directory structures forcertificates.
Note: You need to restart Docker Desktop after making any changes to thekeychain or to the ~/.docker/certs.d directory in order for the changes totake effect.
For a complete explanation of how to do this, see the blog post AddingSelf-signed Registry Certs to Docker & Docker Desktop forMac.
Add client certificates
You can put your client certificates in~/.docker/certs.d/<MyRegistry>:<Port>/client.cert and~/.docker/certs.d/<MyRegistry>:<Port>/client.key.
When the Docker Desktop application starts, it copies the ~/.docker/certs.dfolder on your Mac to the /etc/docker/certs.d directory on Moby (the DockerDesktop xhyve virtual machine).
You need to restart Docker Desktop after making any changes to the keychainor to the
~/.docker/certs.ddirectory in order for the changes to takeeffect.The registry cannot be listed as an insecure registry (see DockerEngine. Docker Desktop ignores certificates listedunder insecure registries, and does not send client certificates. Commandslike
docker runthat attempt to pull from the registry produce errormessages on the command line, as well as on the registry.
Directory structures for certificates
If you have this directory structure, you do not need to manually add the CAcertificate to your Mac OS system login:
The following further illustrates and explains a configuration with customcertificates:
You can also have this directory structure, as long as the CA certificate isalso in your keychain.
To learn more about how to install a CA root certificate for the registry andhow to set the client TLS certificate for verification, seeVerify repository client with certificatesin the Docker Engine topics.
Install shell completion
Docker Desktop comes with scripts to enable completion for the docker and docker-compose commands. The completion scripts may befound inside Docker.app, in the Contents/Resources/etc/ directory and can beinstalled both in Bash and Zsh.
Bash
Bash has built-in support forcompletion To activate completion for Docker commands, these files need to becopied or symlinked to your bash_completion.d/ directory. For example, if youinstalled bash via Homebrew:
Add the following to your ~/.bash_profile:
OR
Zsh
In Zsh, the completionsystem takes care of things. To activate completion for Docker commands,these files need to be copied or symlinked to your Zsh site-functions/directory. For example, if you installed Zsh via Homebrew:
Give feedback and get help
To get help from the community, review current user topics, join or start adiscussion, log on to our Docker Desktop for Macforum.
To report bugs or problems, log on to Docker Desktop for Mac issues onGitHub,where you can review community reported issues, and file new ones. SeeLogs and Troubleshooting for more details.
For information about providing feedback on the documentation or update it yourself, see Contribute to documentation.
Docker Hub
Select Sign in /Create Docker ID from the Docker Desktop menu to access your Docker Hub account. Once logged in, you can access your Docker Hub repositories and organizations directly from the Docker Desktop menu.
For more information, refer to the following Docker Hub topics:
Two-factor authentication
Docker Desktop enables you to sign into Docker Hub using two-factor authentication. Two-factor authentication provides an extra layer of security when accessing your Docker Hub account.
You must enable two-factor authentication in Docker Hub before signing into your Docker Hub account through Docker Desktop. For instructions, see Enable two-factor authentication for Docker Hub.
After you have enabled two-factor authentication:
Go to the Docker Desktop menu and then select Sign in / Create Docker ID.
Enter your Docker ID and password and click Sign in.
After you have successfully signed in, Docker Desktop prompts you to enter the authentication code. Enter the six-digit code from your phone and then click Verify.
After you have successfully authenticated, you can access your organizations and repositories directly from the Docker Desktop menu.
Where to go next
Try out the walkthrough at Get Started.
Dig in deeper with Docker Labs examplewalkthroughs and source code.
For a summary of Docker command line interface (CLI) commands, seeDocker CLI Reference Guide.
Check out the blog post, What’s New in Docker 17.06 Community Edition(CE).
Docker for Mac is a desktop app which allows building, testing andrunning Dockerized apps on the Mac. Linux container images run inside a VM using a custom hypervisor calledhyperkit – part of theMoby open-source project. The VM boots from an.iso and has asingle writable disk image stored on the Mac’s filesystem in the~/Library/Containers/com.docker.docker/Data/com.docker.driver.amd64-linuxdirectory. The filename is eitherDocker.qcow2 or Docker.raw, depending on the format.Over time this file can grow and become large. This post explains
- what’s in the
Docker.raw(orDocker.qcow2); - why it grows (often unexpectedly); and
- how to shrink it again.
If a container creates or writes to a file then the effect depends on the path, for example:
- If the path is on a
tmpfsfilesystem, the file is created in memory. - If the path is on a volume mapped from the host or from a remote server (via e.g.
docker run -vordocker run --mount) then theopen/read/write/… calls are forwarded and the file is accessedremotely. - If the path is none of the above, then the operation is performed by the
overlayfilesystem, ontop of anext4filesystem on top of the partition/dev/sda1.The device/dev/sdais a (virtual)AHCI device, whose code is in thehyperkit ahci-hd driver.The hyperkit command-line has an entry-s 4,ahci-hd,/../Docker.rawwhich configures hyperkit to emulate an AHCI disk device such that when the VM writes to sectorxon the device,the data will be written to byte offsetx * 512in the fileDocker.rawwhere512is thehard-coded sector size of the virtual disk device.
So the Docker.raw (or Docker.qcow2) contain image and container data, written by the Linuxext4 and overlay filesystems.
If Docker is used regularly, the size of the Docker.raw (or Docker.qcow2) can keep growing,even when files are deleted.
To demonstrate the effect, first check the current size of the file on the host:
Note the use of -s which displays the number of filesystem blocks actually used by the file. Thenumber of blocks used is not necessarily the same as the file “size”, as the file can besparse.
Next start a container in a separate terminal and create a 1GiB file in it:
Back on the host check the file size again:
Note the increase in size from 9964528 to 12061704, where the increase of 2097176512-byte sectorsis approximately 1GiB, as expected. If you switch back to the alpine container terminal and delete the file:
then check the file on the host:
The file has not got any smaller! Whatever has happened to the file inside the VM, the host doesn’t seem toknow about it.
Next if you re-create the “same” 1GiB file in the container again and then check the size again you will see:
It’s got even bigger! It seems that if you create and destroy files in a loop, the size of the Docker.raw(or Docker.qcow2) will increase up to the upper limit (currently set to 64 GiB), even if the filesysteminside the VM is relatively empty.
The explanation for this odd behaviour lies with how filesystems typically manage blocks. When a file isto be created or extended, the filesystem will find a free block and add it to the file. When a file isremoved, the blocks become “free” from the filesystem’s point of view, but no-one tells the disk device.Making matters worse, the newly-freed blocks might not be re-used straight away – it’s completelyup to the filesystem’s block allocation algorithm. For example, the algorithm might be designed tofavour allocating blocks contiguously for a file: recently-freed blocks are unlikely to be in theideal place for the file being extended.
Since the block allocator in practice tends to favour unused blocks, the result is that the Docker.raw(or Docker.qcow2Wine for mac powerbook g4. ) will constantly accumulate new blocks, many of which contain stale data.The file on the host gets larger and larger, even though the filesystem inside the VMstill reports plenty of free space.
SSD drives suffer from the same phenomenon. SSDs are only able to erase data in large blocks (where the“erase block” size is different from the exposed sector size) and the erase operation is quite slow. Thedrive firmware runs a garbage collector, keeping track of which blocks are free and where user datais stored. To modify a sector, the firmware will allocate a fresh block and, to avoid the device fillingup with almost-empty blocks containing only one sector, will consider moving some existing data into it.
If the filesystem writing to the SSD tends to favour writing to unused blocks, then creating and removingfiles will cause the SSD to fill up (from the point of view of the firmware) with stale data (from the pointof view of the filesystem). Eventually the performance of the SSD will fall as the firmware has to spendmore and more time compacting the stale data before it can free enough space for new data.
A TRIM command (or a DISCARD or UNMAP) allows afilesystem to signal to a disk that a range of sectors contain stale data and they can be forgotten.This allows:
- an SSD drive to erase and reuse the space, rather than spend time shuffling it around; and
- Docker for Mac to deallocate the blocks in the host filesystem, shrinking the file.
So how do we make this work?
In Docker for Mac 17.11 there is a containerd “task”called trim-after-delete listening for Docker image deletion events. It can be seen via thectr command:
When an image deletion event is received, the process waits for a few seconds (in case other images are beingdeleted, for example as part of adocker system prune) and then runs fstrim on the filesystem.
Returning to the example in the previous section, if you delete the 1 GiB file inside the alpine container
then run fstrim manually from a terminal in the host:
then check the file size:
The file is back to (approximately) it’s original size – the space has finally been freed!
There are two separate implementations of TRIM in Docker for Mac: one for Docker.qcow2 and one for Docker.raw.On High Sierra running on an SSD, the default filesystem isAPFSand we use Docker.raw by default. This is because APFS supportsan API for deallocating blocks from inside a file, while HFS+ does not. On older versions of macOS andon non-SSD hardware we default to Docker.qcow2 which implements block deallocation in userspace which is more complicated and generally slower.Note that Apple hope to add support to APFS for fusion and traditional spinning disks insome future update– once this happens we will switch to Docker.raw on those systems as well.
Support for adding TRIM to hyperkit for Docker.raw was added inPR 158.When the Docker.raw file is opened it callsfcntl(F_PUNCHHOLE)on a zero-length region at the start of the file to probe whether the filesystem supports block deallocation.On HFS+ this will fail and we will disable TRIM, but on APFS (and possibly future filesystems) thissucceeds and so we enable TRIM.To let Linux running in the VM know that we support TRIM we set some bitsin the AHCI hardware identification message, specifically:
ATA_SUPPORT_RZAT: we guarantee to Read-Zero-After-TRIM (RZAT)ATA_SUPPORT_DRAT: we guarantee Deterministic-Read-After-TRIM (DRAT) (i.e. the result of reading after TRIM won’t change)ATA_SUPPORT_DSM_TRIM: we support theTRIMcommand
Once enabled the Linux kernel will send us TRIM commands which we implement withfcntl(F_PUNCHOLE)with the caveat that the sector size in the VM is currently 512, while the sector size on the host canbe different (it’s probably 4096) which means we have to be careful with alignment.
The support for TRIM in Docker.qcow2 is via theMirageqcow2 library.This library contains its ownblock garbage collectorwhich manages a free list of TRIM’ed blocks within thefile and then performs background compaction and erasure (similar to the firmware on an SSD).The GC must run concurrently and with lower priority than reads and writes from the VM, otherwiseLinux will timeout and attempt to reset the AHCI controller (which unfortunately isn’t implemented fully).
Theqcow2 formatincludes both data blocks and metadata blocks, where the metadata blocks contain references to other blocks.When performing a compaction of the file, care must be taken to flush copies of blocks to stable storagebefore updating references to them, otherwise the writes could be permuted leading to the reference updatebeing persisted but not the data copy – corrupting the file.Sinceflushes are very slow (taking maybe 10ms), block copies are done in large batches to spread the cost.If the VM writes to one of the blocks being copied, then that block copy must be cancelled and retried later.All of this means that the code is much more complicated and much slower than the Docker.raw version;presumably the implementation of fcntl(F_PUNCHHOLE) in the macOS kerneloperates only on the filesystem metadata and doesn’t involve any data copying!
Noten zu ich will alles gitte haenning. As of 2017-11-28 the latest Docker for Mac edge version is 17.11.0-ce-mac40 (20561) – automatic TRIMon image delete isenabled by default on both Docker.raw and Docker.qcow2 files (although the Docker.raw implementationis faster).
If you feel Docker for Mac is taking up too much space, first check how many images andcontainers you have with
docker image ls -adocker ps -a
and consider deleting some of those images or containers, perhaps by running adocker system prune):
The automatic TRIM on delete should kick in shortly after the images are deleted and free the spaceon the host. Take care to measure the space usage with ls -s to see the actual number ofblocks allocated by the files.
If you want to trigger a TRIM manually in other cases, then run
To try all this for yourself, get the latest edge version of Docker for Mac from theDocker Store.Let me know how you get on in the docker-for-mac channel of theDocker community slack.If you hit a bug, file an issue ondocker/for-mac on GitHub.